A Secure E – coupon Service Based On Block chain system
First Author1, Second Author2
1 Aruti, Master of Computer Application BKIT-Bhalki
2Prof. Poojarani. N, Master of Computer Application BKIT-Bhalki
Abstract –The widespread use of the electronic coupon (e-coupon) is a direct result of the increasing prevalence of online shopping. Most electronic coupon systems have a central server where all coupon data is stored. However, due of their centralized nature, e-coupon systems often have security difficulties. Examples include double spending (when an expired coupon is used more than once) and fabricated information in the e-coupon database (which is maintained in a central location). To address this problem, we offer a novel e-coupon service that enhances the service’s security by using a blockchain network. We begin by developing a server to facilitate the e-coupon service and exchange data with the blockchain network. Second, we design a blockchain-based smart contract to safeguard the data and business logic behind electronic coupons. The intended service has been built and deployed on Ethereum’s blockchain. Compared to an already available e-coupon service, our testing findings suggest that our proposed service delivers stronger security with a little performance overhead.
Key Words: E-coupon, blockchain, smart contract, security
INTRODUCTION
As the online shopping industry continues to expand, more and more businesses are realizing the potential of electronic coupons (e-coupons) [1, 2]. E-coupons are advantageous for both the merchant (in the form of a store) and the consumer (in the form of a shopper) due to the digital nature of the coupons. For instance, since an e-coupon is a digital code, e-coupon suppliers can simply track how many people are downloading and utilizing their coupons online. In addition, e-coupons may be conveniently managed by clients from their smartphones or computers. Given these benefits of e-coupons, the worldwide mobile coupon industry is expected to expand at a CAGR of 73.14% between 2016 and 2020, as reported by worldwide Mobile Coupons industry 2016-2020.
Despite the growing popularity of electronic coupons and the many advantages they provide, e-coupons are not without their drawbacks. Most e-coupon providers keep track of their coupons in one single location. Electronic coupons are checked against a central database for validity before being accepted at checkout. However, because of the centralized structure of the data, an administrator may quickly alter the information to facilitate forging and fraudulent use of an e-coupon. Double spending is possible with electronic coupons, and the discount rate may be tampered with by an attacker. PennLive reports that the true annual cost of e-coupon crime in the United States is between $300 million and $600 million [4].
Hsueh et al. [5] propose an e-coupon system that combines a hash chain with blockchain technology to improve e-coupon security. When it comes to protecting e-coupon data using blockchain technology, our research is consistent with existing efforts. In contrast, we ensure both the operational (such as e-coupon management) and data (pertaining to e-coupons) integrity by developing a robust smart contract.
LITERATURE SURVEY:
E-coupons are growing in popularity as a form of promotion because to the Internet’s convenience and speed. Electronic coupons, or “e-coupons,” are the online equivalent of traditional paper coupons that may be redeemed for discounts or freebies in order to encourage consumers to make a purchase. The internet’s potential for digital discounts is now underutilized. Because there aren’t any “efficient” methods for managing the creation and distribution of e-coupons, this is the case. In this work, we cover the concepts and methods for secure electronic coupons. In addition, we provide a lightweight version of our protocol that protects users’ anonymity by skipping the registration step.
Blockchain is a distributed, immutable database that may be used to create digital versions of traditionally paper-based records including birth certificates, property deeds, academic transcripts, medical records, and election results. discounts have long been used in corporate promotion, and with the rise in use of mobile devices, digital discounts are progressively replacing physical coupons. Peer-to-Peer (P2P) sharing and increased coupon utilization via peer trusts have been sparked by the strong relationships between individuals and the use of mobile coupons. Promoting the transfer of unused mobile discounts to future users may be facilitated by adding extra feedback systems.
Security concerns like forgery or manipulation must be prevented from compromising the vital information included in mobile coupons, such as the contents and the feedback incentive. In general, powerful security methods used on desktop computers can’t be implemented on mobile devices due to constraints in storage space, CPU power, and transmission bandwidth. Hash Chain is paired with blockchain technology in this research to validate counterfeit coupons and to facilitate the storing and transfer of data that requires little in the way of processing. Our system embodies the P2P collaborative spirit inherent in blockchain’s decentralized architecture. In a P2P setting, the dispersed miners do the verifications, lowering the possibility of collusion between malicious actors. The suggested approach ensures the complete security of communications by using blockchains, which are anonymous and so immune to eavesdropping.
The importance of using sound design principles while creating a website is rising. The authors use this methodology inside a framework for layered architectures predicated on the model-view-controller pattern popularized by the Smalltalk graphical user interface development environment.
Direct online payments might be made from one person to another without going through a bank using a peer-to-peer electronic currency system. If a trustworthy third party is still needed to avoid double-spending, then digital signatures are just a partial answer.
We suggest a peer-to-peer network as a means of resolving the double-spending issue.
To create an immutable record of all past transactions, the network hashes them into a continuously growing chain of hash-based proof-of-work. The longest chain not only proves the order of events, but also indicates the source of the most computational resources. To outrun attackers, the longest chain must be generated by nodes that are not working together to launch a coordinated assault on the network. The network architecture is rather simple. While nodes are free to quit and rejoin the network at any time, they must accept the longest proof-of-work chain as evidence of what occurred during their absence.
SCOPE OF THE WORK:
We prioritized tightening up security by checking every e-coupon information for correctness. For instance, the present electronic coupon service relies on a database. A rogue administrator might easily alter data in this system because of how easy it is to get administrative privileges. Since consensus among all users is required for the administrator of our provided service’s block chain system to obtain power, this might be a challenge. Therefore, we can prevent unauthorised alteration and power grabs are more difficult. This shows that the proposed approach improves security. In section IV-C, we delve into further depth. Keep in mind the many investigations towards bettering the block chain’s capabilities. Therefore, future block chain performance difficulties will be mitigated, and efforts to further improve block chain performance will be postponed.
SYSTEM ANALYSIS:
Existing System: E-coupon use has increased with the popularity of smartphones and the rise of online shopping. When compared to paper coupons, e-coupons make it simpler for coupon suppliers to track and manage data about their coupons (such as the number of coupons available, the number of downloads, client lists, and the redemption status of individual coupons). E-coupons also allow users to utilize and
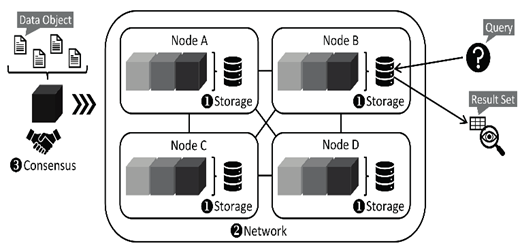
manage their coupons from any computer or mobile device. Since data stored in a centralized server can be controlled and gathered quickly, as illustrated in Figure 1, most e-coupons are given by such a server.
PROPOSED SYSTEM
To address this issue, we suggest a blockchain-based e-coupon service. First, we’ll be designing a server to support e-coupon redemption. 21836 This is an open-source project that you are free to share and adapt with proper attribution. If you want to learn more, Blockchain-Based Electronic Coupon Service for Safety and Convenience Fig.1 A sample of a consolidated electronic coupon service. and talk to the blockchain network. Second, we create a blockchain-based smart contract for e-coupons to ensure the security of transactions (the business logic code) and e-coupon data.
ARCHITECTURE
CONCLUSION:
We looked at e-coupon services where the data for all the coupons is kept in one place. We discovered that a server administrator or hacker might potentially change the e-coupon data saved on the server. To address this problem, we provide a novel e-coupon service that tightens up security by using smart contracts to track e-coupons throughout a blockchain network.
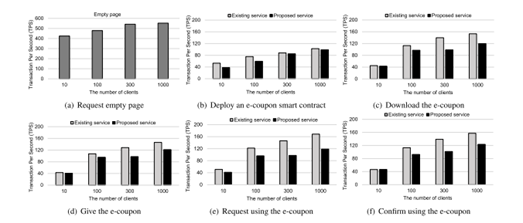
The proposed service has been built and tested on the Quorum blockchain, and its performance has been measured against a synthetic benchmark. Our experiments show that the proposed service effectively avoids the manipulation of e-coupon information with improved security and little impact on system performance. Enhancing blockchain functionality is a future priority.
RELATED WORK
For the purpose of delivering a safe electronic voucher, there have been prior research [2, [12], [13], [15]. For the purpose of e-coupon safety, Blundo et al. [2] present novel e-coupon models and e-coupon protocols that make use of message authentication code (MAC). Double-spending may be avoided with the use of a central coupon mint, as proposed by Agarwal et al. [12]. Hsueh et al. [13] employ digital signatures (i.e., PKI) to sign the e-coupon and hash functions to validate all digital signatures of the e-coupon and ensure the information is consistent.
Using a one-way hash function and a message authentication code (MAC), Chang et al. [15] have developed a method for preventing users from redeeming an electronic discount more than once.
A user may tell whether an electronic voucher has been tampered with by a hacker by using one of the methods described in [2, [12], [13], or [15]. As a result, they control the distribution and redemption of electronic coupons while preventing their misuse. However, when information about an e-coupon may be changed in the e-coupon server database, none of these methods are appropriate. What’s more, these methods do nothing to stop an administrator from acting maliciously. When it comes to strengthening the safety of electronic coupons, our research is consistent with prior publications [2], [12], [13], [15].
On the other hand, we’re working to make it harder for people to steal legitimate electronic coupons and more difficult to create fake ones.
To check whether electronic coupons have been counterfeited, Hsueh et al. [5] present a hash chain that is integrated with blockchain technology. Using blockchain technology, they ensure that all data associated with electronic coupons is accurate. In terms of leveraging blockchain technology for e-coupon integrity, our research is consistent with the work [5]. Instead, we use a smart contract to ensure that all the business logic around electronic coupons—including their distribution, redemption, and distribution as gifts—remains entirely trustworthy.
REFERENCES
[1] (2019). Wikipedia: E-coupon. [Online]. Available: https://en.wikipedia. org/wiki/E-coupon
[2] C. Blundo, S. Cimato, and A. De Bonis, ‘‘Secure E-coupons,’’ Electron. Commerce Res., vol. 5, no. 1, pp. 117–139, Jan. 2005.
[3] (2016). World Mobile Coupons Market to Grow at 73.1% CAGR to 2020. [Online]. Available: https://www.prnewswire.com/newsreleases/world-mobile-coupons-market-to% -grow-at-7314-cagr-to-2020- 603320306.html
[4] (2017). Coupon Fraud is Crime, Even if it Feels Harmless: Coupon Counselor. [Online]. Available: https://goo.gl/2emab1.
[5] S.-C. Hsueh and J.-H. Zeng, ‘‘Mobile coupons using blockchain technology,’’ in Proc. Int. Conf.
Intell. Inf. Hiding Multimedia Signal Process. Springer, 2018, pp. 249–255.
[6] A. Knight and N. Dai, ‘‘Objects and the web,’’ IEEE Softw., vol. 19, no. 2, pp. 51–59, Mar. 2002.
[7] (2018). Quorum. [Online]. Available: https://github.com/jpmorganchase/ quorum
[8] (2017). Coupon Statistics: The Ultimate Collection. [Online]. Available: https://blog.accessdevelopment.com/ultimate-collection-couponstatistic%s
[9] (2017). emphDigital Coupon Marketing—Statistics and Trends. [Online]. Available: https://www.invespcro.com/blog/digital-coupon-marketing
[10] (2019). Digital Coupons Continue to be the Fastest Growing Method of Redemption due to Shoppers’ Increased Demand for Convenience. [Online]. Available: https://www.globenewswire.com/news-release/2019/ 02/13/1724510/0/en/Digi%tal-Coupons-Continue-to-be-the-FastestGrowing-Method-of-Redemption-Due-to-Sho%ppers-IncreasedDemand-for-Convenience.html